
Apple’s track record is rather clean when it comes to maintaining security for its Macs. However, a newly found goof-up might screw up its impressive scorecard.
The company accidentally approved an Adobe Flash-based malware to run on Macs without any warning. Security researchers Patrick Wardle and Peter Dantini found this bug in a Flash-powered installer hosted on a copycat site of Homebrew, a package management system for Linux.
To ensure that apps running on macOS are secure, Apple asks developers for what’s called a Notarization process. If the company’s automated service finds that the app doesn’t have any malware, it issues a ticket for the developer to attach with the software. That ticket is used when you install that app on your Mac, so the system can identify it as a safe app.
If the app doesn’t pass the test, the system shows a warning as shown in the diagram below. You can read more about the Noteraization process here.
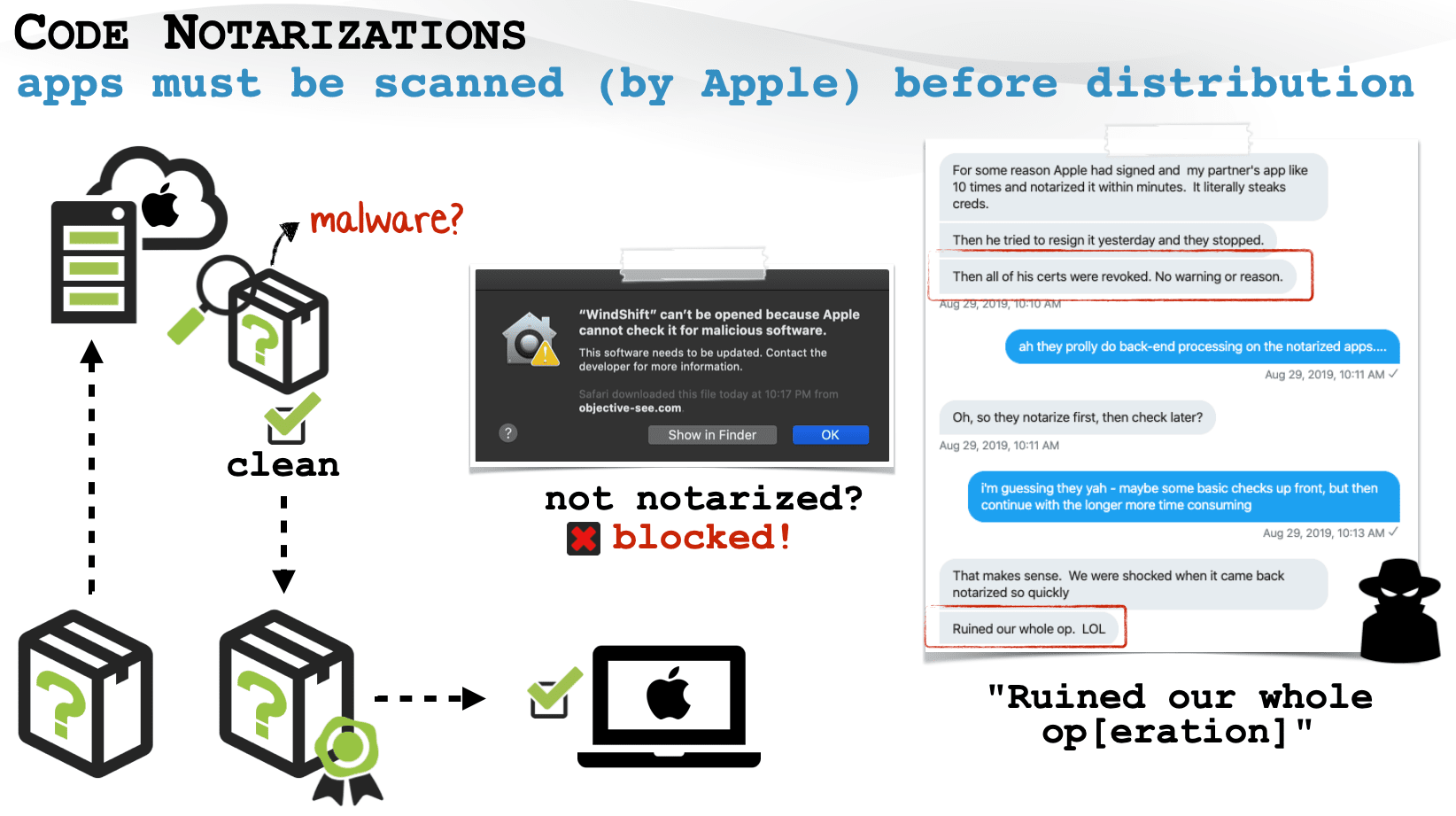
Wardle and Dantini found that Apple has notarized this common type of malware, and it can run on macOS without any warning. The duo noted in a blog post that this means the company found no malicious code in this installer, and it can even run on the newest version of macOS, Big Sur. Plus, because this malware was ‘Apple-certified’ users would install it without checking.

The malware doesn’t steal any data but acts as adware. So, it’ll generate a lot of ads on your screen to earn money and hog up your system’s resources. It also throws up ads on pages that are protected through HTTPS encryption.
Apple said in a statement that it has revoked the certificate of the payload and disabled the malicious actor’s developer account:
Malicious software constantly changes, and Apple’s notarization system helps us keep malware off the Mac and allow us to respond quickly when it’s discovered. Upon learning of this adware, we revoked the identified variant, disabled the developer account, and revoked the associated certificates. We thank the researchers for their assistance in keeping our users safe.
The company has also blocked new notarized payloads deployed by the attackers. Thankfully, as a user, you don’t have to do anything in case you’ve installed these payloads.
So you like TNW? Then join our upcoming online event, TNW2020, you don’t want to miss it.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




