
The intricate mobile malware campaign targeting the Uyghur Muslim minority in China was also directed at senior members of Tibetan groups, according to new research.
The details — disclosed by University of Toronto’s Citizen Lab and TechCrunch — reveal that the targets were sent specifically tailored malicious web links over WhatsApp, which, when opened, exploited browser vulnerabilities on iOS and Android devices to install spyware, and surreptitiously steal private and sensitive information.
The researchers have traced the campaign back to a single operator they call POISON CARP.
“The campaign is the first documented case of one-click mobile exploits used to target Tibetan groups,” Citizen Lab said. “It represents a significant escalation in social engineering tactics and technical sophistication compared to what we typically have observed being used against the Tibetan community.”
Social engineering on WhatsApp
Attempts to infect targets arrived in the form of WhatsApp messages from seven fake personas masquerading as journalists, staff at international advocacy organisations, volunteers to Tibetan human rights groups, and tourists to India.
The social engineering attacks — detected between November 11-14 last year — lured their targets to click on a link that was masked behind URL shorteners, which redirected to a malware-infested page that leveraged an iOS exploit chain affecting versions 11.0 through 11.4. Apple issued a fix for the flaw with iOS 11.4.1 in July 2018.
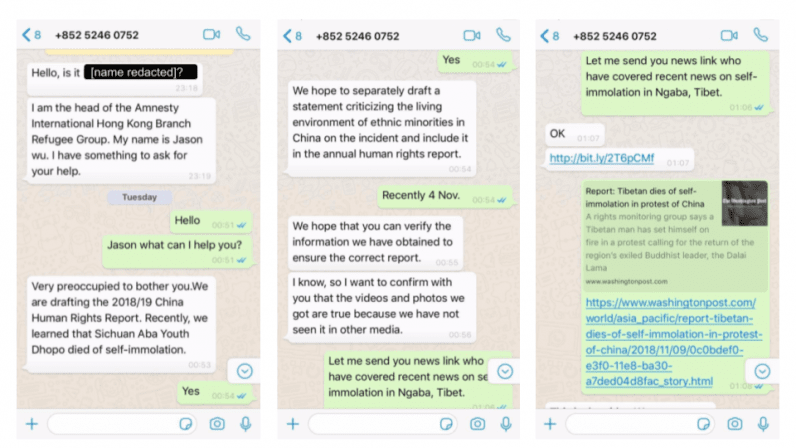
Fortunately, none of the individuals who clicked on the malicious links were compromised as they were running non-vulnerable versions of iOS or Android.
The exploits share a number of similarities with the recently discovered targeted malware campaign aimed at Uyghur Muslims in that the iOS exploit and spyware discovered by Citizen Lab was also employed in the watering hole attacks described by Google’s Project Zero team last month.
Although Google didn’t reveal any details about the targets or the actors behind the operation, Apple — which has since patched the vulnerabilities — issued a rare statement confirming the exploits targeted Uyghurs while disputing the scale of the attack.
The findings also overlap with a Volexity report earlier this month, which published details of an Evil Eye cyberespionage campaign against Uyghurs that used compromised websites to infect targets with Android malware.
Similarities in spyware
Noting the likeness with the iOS spyware implant described by Google Project Zero researchers, Citizen Lab stated that “the two implants represent the same spyware program in different stages of development,” with the November 2018 version depicting an earlier phase, lacking in capabilities to carry out large-scale digital snooping.
Once installed, the spyware was found to extract device information and data from a hard-coded list of apps like Viber, Telegraph, Gmail, Twitter, QQMail, and WhatsApp. It’s worth noting that the list uncovered by Project Zero also included Skype, Facebook, WeChat, Outlook, and Yahoo! Mail.
In addition, POISON CARP exploited a total of 8 distinct Chrome browser exploits in Android (affecting versions 39 to 73) to install a previously undocumented Android spyware called MOONSHINE, which siphoned SMS text messages, address books, and call logs, aside from snooping on the targets through their phones’ camera, microphone, and GPS.
“Beyond the technical overlap in these campaigns is the fact that they all targeted ethnic minority groups related to China: Uyghurs and Tibetans,” Citizen Lab said. “However, the level of threat posed by POISON CARP and the linked campaigns are a game changer.”
If anything, the three campaigns demonstrate the evolving tactics of the cyberattack machine put together by Chinese threat groups, and most importantly, the extensive demand for exploitation of mobile devices. As handheld gadgets increasingly become a lucrative attack surface, the need to fortify against such threats cannot be overstated enough.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





