
Cybersecurity researchers have discovered a new strain of the nefarious Glupteba malware that uses the Bitcoin blockchain to ensure it remains dangerous.
TrendMicro’s latest blog details the previously undocumented variant which is capable of invading systems to mine Monero cryptocurrency and steal sensitive browser data like passwords and cookies.
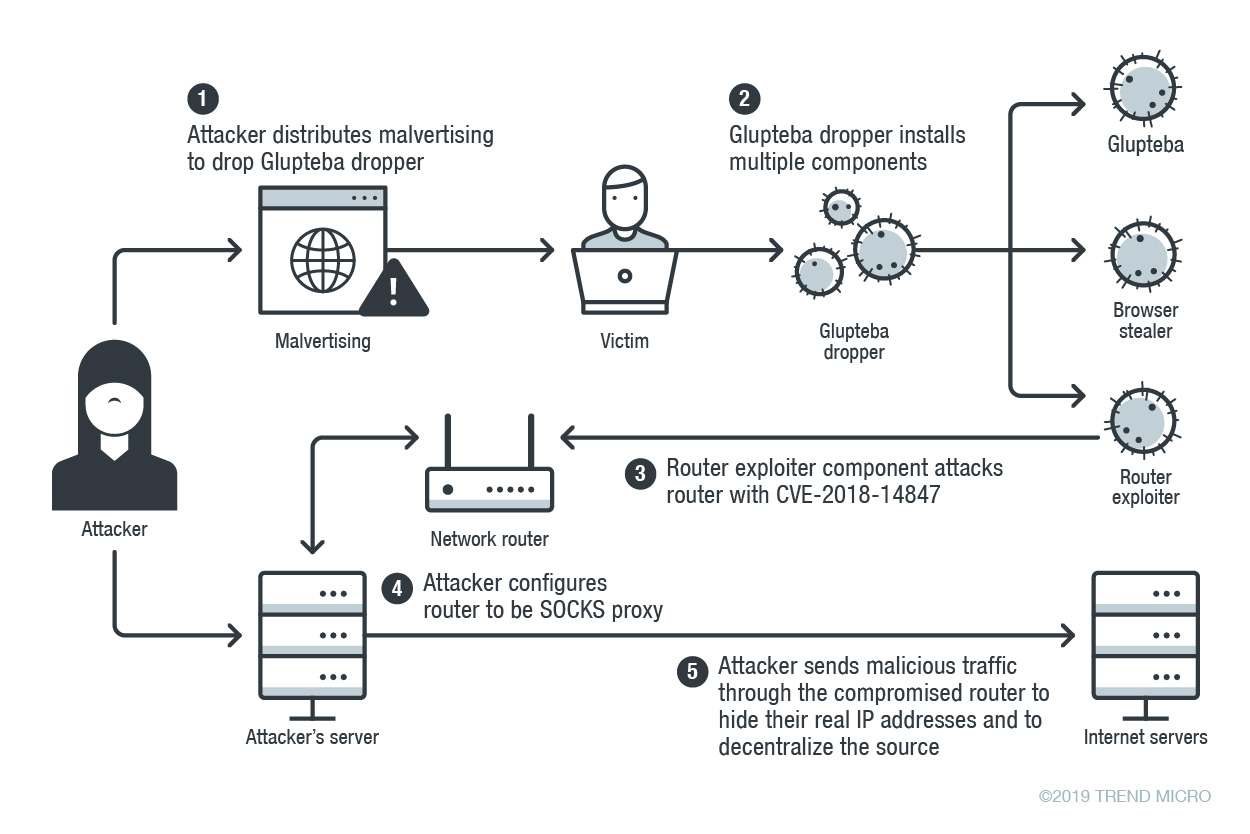
Analysts confirmed this version of Glupteba also exploits an already-discovered security vulnerability in MicroTik routers to transform the target machine into a SOCKS proxy to initiate widespread spam attacks that could threaten Instagram users.
Attackers transfer Bitcoin with Electrum to keep Glupteba online
Infection typically works like this: a target machine is first hit with a “malvertising attack,” which forces it to download a Glupteba “dropper.”
The dropper will flood the target with various rootkits, backdoors, and other nasties taken from GitHub. It then does the usual stuff like check for antivirus programs, add malicious firewall rules, as well as include itself in defender whitelists.
Most notable, however, is that this malware utilizes Bitcoin to automatically update, ensuring it runs smoothly even if antivirus software blocks its connection to remote command and control (C&C) servers run by the attackers.
According to TrendMicro researchers, Glupteba goons will first send Bitcoin transactions via the Electrum Bitcoin wallet, which Hard Fork previously reported had been threatened by a prolific phishing campaign.
The malware, which has been programmed with a hardcoded ScriptHash string, will then make its way through a public list of Electrum servers to find every transaction that was made by the attacker.
Buried in those transactions is seemingly innocent OP_RETURN data which contains an encrypted C&C domain. The ScriptHash string is then used to decrypt that data.
“This technique makes it more convenient for the threat actor to replace C&C servers,” said TrendMicro. “If they lose control of a C&C server for any reason, they simply need to add a new Bitcoin script and the infected machines obtain a new C&C server by decrypting the script data and reconnecting.”
To ensure your machine is protected against innovative threats like Glupteba, DON’T CLICK ON SUSPICIOUS LINKS AND EMAILS. Also, ensure your router’s firmware is up-to-date. Be safe out there.
Get the TNW newsletter
Get the most important tech news in your inbox each week.



