
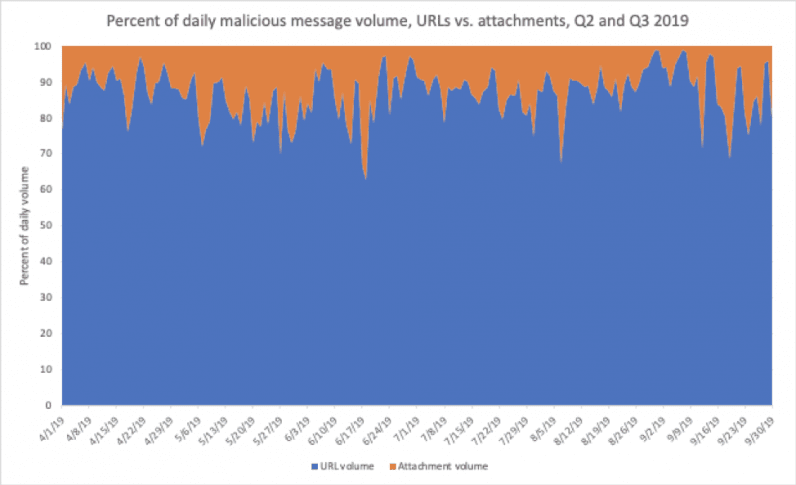
Emails containing malicious URLs made up 88 percent of all messages with malware-infested links and attachments, underscoring the dominance of URL-based email threats.
The findings — disclosed in cybersecurity firm Proofpoint’s quarterly threat report for the month ending September — reveal the evolving sophistication of social engineering attacks targeting users and organizations.
“Email-based threats are among the oldest, most pervasive, and widespread cybersecurity threats hitting organizations worldwide,” Chris Dawson, Threat Intelligence Lead at Proofpoint, told TNW.
“From massive malware campaigns targeting millions of recipients with banking Trojans to carefully crafted email fraud, the email threat landscape is extremely diverse, creating a wide range of opportunities for threat actors to attack organizations,” Dawson added.
Some other key trends to note are the prevalence of sextortion campaigns, and the notable absence of Emotet botnet spam and ransomware attacks propagated via malicious emails.
“Ransomware is still a threat,” Dawson stated. “However, with rapidly dropping cryptocurrency valuations, threat actors are having a harder time monetizing their ransomware campaigns. Instead they are turning to ‘quieter’ infections with banking Trojans and downloaders that can potentially sit on infected machines for extended periods, collecting data, mining cryptocurrency, sending spam, and more.”
Indeed, overall message volumes of banking Trojans (Trickbot, IcedID, Ursnif) and remote administration tools (FlawedAmmy, FlawedGrace) increased by 18 percent and 55 percent when compared to the previous quarter — all deployed with an aim to evade detection and stealthily collect credentials, conduct reconnaissance, move laterally on networks, and enable at-will distribution of secondary payloads.
The re-emergence of Emotet
Emotet, for its part, didn’t completely go away. Dubbed “TA542” by Proofpoint researchers, the botnet-driven spam campaign, has recently emerged as the biggest source of destructive malware, morphing from its original roots as a banking Trojan to a “Swiss Army knife” that can serve as a downloader, information stealer, and spambot depending on how it’s deployed.
While the malware appeared to have largely disappeared throughout the summer of 2019, it made a comeback in September via “geographically-targeted emails with local-language lures and brands, often financial in theme, and using malicious document attachments or links to similar documents, which, when users enabled macros, installed Emotet.”
Interestingly, Emotet’s re-awakening in the last two weeks of the month ended up accounting for 12 percent of all malicious payloads for the entire third quarter. This also coincides with a similar report published by Netscout early this week:
In May 2019, Emotet’s activity started to decline. This hiatus lasted for approximately four months when it made a resurgence in September 2019. The activity picked up as if it never left with evolving spam campaigns and new delivery mechanisms.
It’s worth noting that Emotet amounted to almost two-thirds of all payloads delivered through phishing emails between January and March 2019.
What’s also shifted are the countries impacted: in addition to its longstanding targets, such as the US, the UK, Canada, Germany, and Australia, TA542 expanded vastly in scope to encompass Italy, Spain, Japan, Hong Kong, and Singapore.
Mitigating social engineering attacks
Protecting organizations from phishing attacks mandates a “multi-layered approach” that starts with securing the email channel, and identifying and protecting the most attacked individuals.
“To truly determine risk, organizations must weigh the sheer number of threats received by each user, where those attacks are coming from, how targeted each attack is, and what type of malware is involved in each attack,” Dawson told TNW.
“Using this insight, organizations can implement user-centric adaptive access controls based on the user’s role, considering certain privileges and VIP status, the risk level associated with the login, and other contextual parameters such as user’s location, device hygiene, and others,” he said.
That’s not all. It also requires training employees to spot phishing campaigns that target them and help them understand why they are at risk.
“Training employees on what to click is useful,” Adrien Gendre, Chief Solution Architect at predictive email defense firm Vade Secure, told TNW. “But the current form of training alone is not adequate. It’s of little use when attackers keep changing their techniques every few months. It needs to be contextualized so that employees can identify malicious content when they see it.”
What’s needed, therefore, are appropriate security controls, whether be it static, behavioral, or machine learning based, that can act as an email gateway to stop such social engineering attempts from reaching their targets’ inboxes and provide ways to recover from them if they get through.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




