Security researchers have found a new phishing campaign that leverages fake voicemail messages to trick victims into stealing their Office 365 email credentials.
The scam — uncovered by cybersecurity firm McAfee — made use of fraudulent email attachments, which when opened, redirected users to a phishing website that siphoned the login information with an aim to impersonate staff members and gain wider access to internal systems.
A number of employees, from middle management to executive level staff employed across different verticals such as services, finance, IT services, retail, and insurance, were targeted in what the researchers call a whaling campaign.
This can have serious consequences if the victim in question is reusing the same password, thereby leaving them open to more targeted attacks.
“The goal of malicious actors is to harvest as many credentials as possible, to gain access to potentially sensitive information and open the possibility of impersonation of staff, which could be very damaging to the company,” McAfee researchers said.
Office 365 is a line of subscription services offered by Microsoft that includes Microsoft Office as as well as cloud-based software as a service products for business environments, such as hosted Exchange Server, Skype for Business Server, and SharePoint, among others.
The attack begins with the victim receiving an email — containing an HTML file as an attachment — informing them that they have missed a phone call, along with a request to login to their account to access their voicemail.
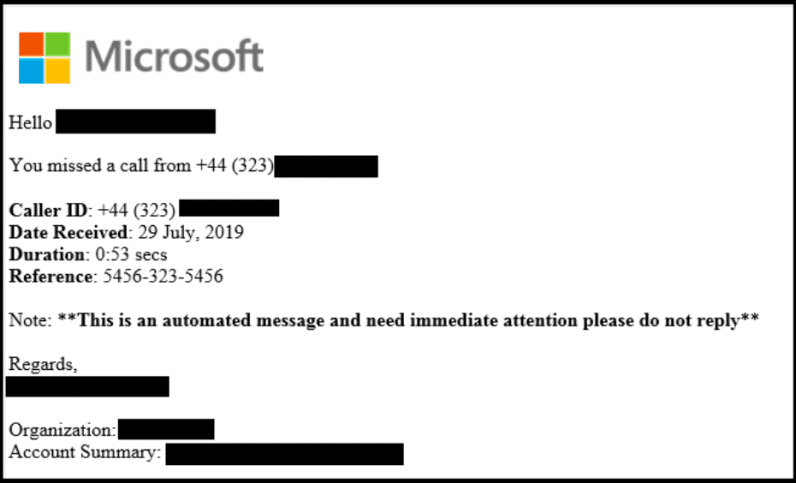
This HTML file, when loaded, auto-plays a fake voicemail message, while redirecting the user to a phishing website that prompts the individual to sign in to their accounts. To give the rogue website an air of legitimacy, the email address is also prepopulated in the landing page, thereby increasing the chances of social engineering the victim.
Upon entering the passwords, users receive a successful login message and are redirected to the legitimate office.com website. The harvested data — including email addresses, passwords, IP addresses, and locations — is then emailed to the owner of the phishing site.
It’s a known fact that criminals are constantly finding new ways to lure users to steal their information. With over 180 million monthly active users, Microsoft Office 365 has become a target-rich environment for sophisticated phishing attacks, making it the number one phished brand, according to predictive email defense firm Vade Secure.
Describing a similar phishing campaign which it called “the voice message attack,” the company said “the phishing link could send you to a Microsoft login screen that looks perfectly real, except it’s not. It’s a phishing site designed to steal your Office 365 login credentials.”
If anything, the attacks are a sign that two-factor authentication is essential to securing accounts from unauthorized access and be vigilant when it comes to opening emails and attachments from unknown senders.
This also underscores the need for adopting appropriate anti-phishing measures to stop social engineering attempts from reaching their targets’ inboxes — such as blocking those with “.html” and “.htm” attachments — and training people to spot mails that get through.
“What sets this phishing campaign apart from others is the fact that it incorporates audio to create a sense of urgency which, in turn, prompts victims to access the malicious link. This gives the attacker the upper hand in the social engineering side of this campaign,” the researchers concluded.
Get the TNW newsletter
Get the most important tech news in your inbox each week.





