Technology has brought great advances and conveniences, but it also comes with the cost of privacy. You;ve seen many examples in the news. The NSA has been caught spying on German chancellor Angela Merkel and her closest advisers for years. WikiLeaks co-founder Julian Assange says the NSA intercepts 98 percent of South American communications.
You’d fight for free speech if anyone threatened to take it away. Yet ISPs, technology companies, and the government are all threatening to take away our privacy, and we’re standing by and letting it happen. Even if you have nothing incriminating to hide, you still have sensitive information on the internet, and the right to privacy.
Here are some of the organizations that are spying on you, and some of the simple steps you can take to protect yourself and your information.
Who’s spying on us?
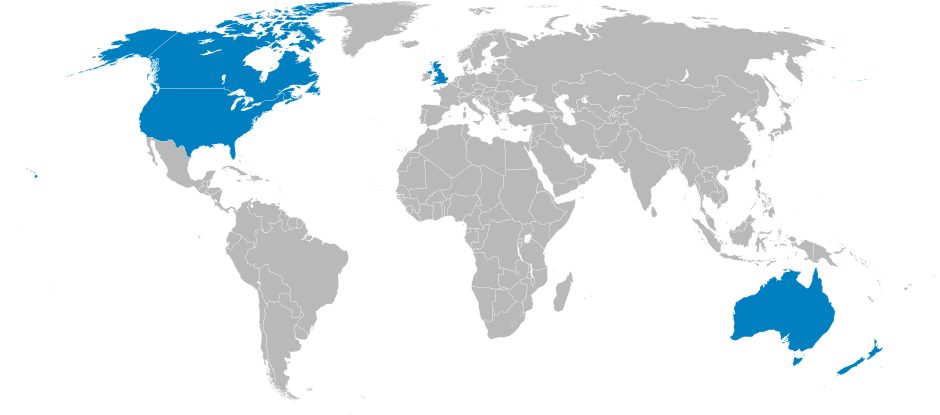
Few organizations have caught as much of the spotlight as the National Security Agency (NSA). But even outside of the States, many governments have their own version of the NSA.
The most prominent ones are:
- UK’s Government Communications Headquarters (GCHQ)
- Communications Security Establishment Canada (CSEC)
- Australian Signals Directorate (ASD)
- New Zealand’s Government Communications Security Bureau (GCSB)
Together with the NSA, they form the Five Eyes alliance. These government organizations regularly collaborate on spy programs with silly code names, but their work is no laughing matter.
The government can call upon technology companies to learn about you. Although technology companies wouldn’t want to rat out their own customers, they may simply have no choice. Yahoo CEO Marissa Mayer said executives faced jail if they revealed government secrets. Google has even made a petition for greater transparency.
So technology companies are forced to work with the government. Yahoo has complied with government requests for information.
Technology companies know quite a bit about you
Google snuck code into advertisements that would install tracking cookies into users’ devices without their knowledge. Through Android, Google knows nearly every Wi-Fi password in the world.
Both Apple and Google track your phone’s movements with location-based services. Google scans your emails in order to serve you more relevant advertisements. Apple stores your iMessages. Dropbox reads your files.
As if jail wasn’t compelling enough, the government is also rumored to spy on technology companies.
“It’s really outrageous that the National Security Agency was looking between the Google data centers, if that’s true,” said Google’s Executive Chairman Eric Schmidt to the Wall Street Journal. “The steps that the organization was willing to do without good judgment to pursue its mission and potentially violate people’s privacy, it’s not OK.”
Even if you have nothing to hide, you have the right to your privacy. Here’s how you can protect your data from prying eyes.
How can you protect ourselves from people spying on you?

Before we proceed, it’s important to hammer this point home: there is no protection or system that is completely, 100 percent guaranteed, safe from hackers. Given enough time and money, an experienced hacker can hack into any system. (There are people attempting to create a system that can’t be hacked for 100 years.)
Surveillance organizations and technology companies have both time and money. That means yes, they could hack into your computer if they were specifically targeting you. However, it’s unlikely they’d dedicate their resources to zero in on the average citizen. It would cost them too much time and money if they scaled that up across the board.
Imagine if every citizen made it more difficult (and therefore expensive) for these organizations to spy on them. It would become more expensive for these programs to keep an eye on everyone. That would make it more difficult for them to keep a close eye on the majority of people.
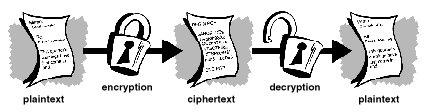
A simple, but fundamental, step to privacy is to encrypt your data. Whether it’s the government or some hacker spying on you, encryption makes your information way harder to read.
Encryption codes the information that’s transferred between you and the website you’re visiting. Any prying eyes (e.g., the government, hackers, etc.) have to put more time and energy into decoding the encrypted information before they can read it.
The next time you use your Web browser, have a look at the URL bar. You can tell your communication with a website is encrypted when there’s a green padlock and an “https://” preceding the website address.
Although many sites support HTTPS, some of them may not enable it by default (keeping you on an unencrypted http:// connection). Use a plugin like HTTPS Everywhere to ensure you connect via HTTPS as often as possible.
Some padlocks also feature a company’s name beside it (like PayPal, Inc.). That means the company has an extended verification certificate, which provides the strongest encryption level available (and requires more rigorous testing and validation).
You can add an extra layer of encryption to your data by browsing through a Virtual Private Network (VPN). “The first thing I’d recommend to the average person on the street is whenever you’re out in the public…use a VPN service,” says former “Most Wanted Hacker” Kevin Mitnick in an interview.
“It takes your data and puts it in an encrypted envelope so people can’t really intercept it and spy on that.”
Also, put your data in the hands of technology companies that encrypt it. Edward Snowden, for example, recommends using SpiderOak instead of Dropbox (or at least protect your Dropbox folders with Truecrypt). You could use DuckDuckGo instead of Google. (If you miss Google’s powerful search algorithm, just use the !g function in DuckDuckGo.) Chat with OTR instead of Skype.
There are tons of alternatives that likely protect your data better than the software you’re using.
Have a look at this privacy pack put together by Reset the Net. Keep your eyes peeled for technology that uses end-to-end encryption. End-to-end encryption ensures that your data only gets decrypted once it’s opened by the recipient, meaning that the technology companies wouldn’t be able to read the data in transit even if they were forced to pass it along to the government. You know it’s probably effective as the FBI and Department of Justice want companies to ease off end-to-end encryption.
How do the pros protect their information?
It’s tough to find people that protect their privacy well as they don’t tend to advertise themselves online. There are certain experts like journalists and security specialists that work with sensitive information.
As such, they’ve set up systems to protect their information as much as possible. You can use their methods to set up a more secure system of your own.

The NSA can’t read the information on your computer if you’ve never been connected to the Internet. If you have extremely sensitive information, consider investing in a computer that’s never touched the Internet (known as an “airgap”).
Columnist Bruce Schneier writes at The Guardian:
Since I started working with the Snowden documents, I bought a new computer that has never been connected to the Internet. If I want to transfer a file, I encrypt the file on the secure computer and walk it over to my Internet computer, using a USB stick. To decrypt something, I reverse the process. This might not be bulletproof, but it’s pretty good.
If you plan to use an airgap, you might also want to remove any network chips, bluetooth chips, or even microphones and webcams from your new computer before using it.
Along a similar vein, you could also use an operating system that’s bootable from a USB drive, and browse incognito. Tails is an operating system which forgets your activities after you unplug. Journalists working with Edward Snowden relied on it for secure communication.
“Privacy and encryption work, but it’s too easy to make a mistake that exposes you,” writes journalist Barton Gellman. “Tails puts the essential tools in one place, with a design that makes it hard to screw them up. I could not have talked to Edward Snowden without this kind of protection. I wish I’d had it years ago.”
Tails allows you to use GPG encryption when you are emailing and/or OTR encryption while instant messaging, with little setup required. These types of encryption come recommended by CDT’s senior staff technologist, Joe Hall.
GPG and PGP encryption are standards that allow you to encrypt and decrypt files and emails using a public/private keypair. (Here’s an intro to how PGP and cryptography work.)
Tails also allows journalists to work on sensitive documents, edit audio and video, and store all their files in an encrypted format. Additionally, Tails routes your web connections through the Tor network by default. The Tin Hat explains Tor pretty simply:
Tor offers a great degree of anonymity and privacy by encrypting your Internet connection and sending it through three servers placed around the globe.
In case you’re curious to learn more, we’d suggest going deeper into how journalists and security specialists handle sensitive information. For example, learn from this article how Edward Snowden leaked his information to the world. (Here’s another one.)
If you have some sensitive information that you want to share with the press, use an encrypted service like SecureDrop.
Start with the basics
There’s a lot of information in this piece. Don’t drive yourself crazy with paranoia. Just remember that it all starts with making your information a bit more difficult to read through encryption. Use software that has end-to-end encryption built-in. VPNs are a simple solution that quickly ensure your information is at least a bit more challenging to read.
If you ever do want to turn your privacy up a notch, encrypt emails with crypto technology and use airgaps and encryption-focused operating systems.
Even if you have nothing to hide, you have the right to privacy. It’s your responsibility to protect it while you still can.
Arthur Baxter is an Operations Network Analyst at ExpressVPN, a VPN provider offering over 97 different servers in 78 countries.
Read next: How to stop hackers from stealing your information on public Wi-Fi
Get the TNW newsletter
Get the most important tech news in your inbox each week.