
The US Department of Justice (DOJ) today unsealed indictments against a pair of Chinese agents charged with hacking US computer systems from a period spanning 2006 – 2018. Among those successfully targeted was the US Navy.
Personally identifiable information including, social security numbers, names, and phone numbers pertaining to at least 100,000 US Navy service members was allegedly stolen during the espionage campaign.
The FBI and DOJ have identified the defendants as Zhu Hua and Zhang Shilong, alleged members of a Chinese state-sponsored hacking group.
According to the unsealed documents:
Over the course of the Technology Theft Campaign, the defendants and their coconspirators successfully obtained unauthorized access to at least approximately 90 computers belonging to, among others, commercial and defense technology companies and US Government agencies located in at least 12 states, and stole hundreds of gigabytes of sensitive data and information from their computer systems …
The FBI, DOJ, and most media outlets are characterizing the campaign as an intellectual property-theft (IPT) issue, alleging the Chinese agents’ intent was to steal technology plans.
According to the FBI’s wanted poster for the group, known as Advanced Persistent Threat 10 (APT 10), or Cloudhopper, the group’s effort was massive:
As alleged in the Indictment, from at least 2006 through 2018, the defendants conducted extensive campaigns of global intrusions into computer systems aiming to steal, among other data, intellectual property and confidential business and technological information from more than at least 45 commercial and defense technology companies in at least a dozen states, managed service providers (“MSP”), which are companies that remotely manage the information technology infrastructure of businesses and governments around the world, and U.S. government agencies.
All of that is terrifying. Taken at face value, the information released today tells us that China likely has incredibly detailed knowledge pertaining to a significant number of US technology secrets.
But what about those 100,000 sailors’ personal information?
Let’s pause for a moment and point out the obvious: there’s not enough information currently available to make any specific determinations. If the DOJ says this is an IPT case, it’s an IPT case. We’re not trying to start a conspiracy theory that the Chinese government has access to US Navy top secret information. Because it probably doesn’t. It’s the unclassified info that concerns us.
Our worry stems from some of the statements in the indictment. Here’s what’s bothering us (box and underlining added by TNW):

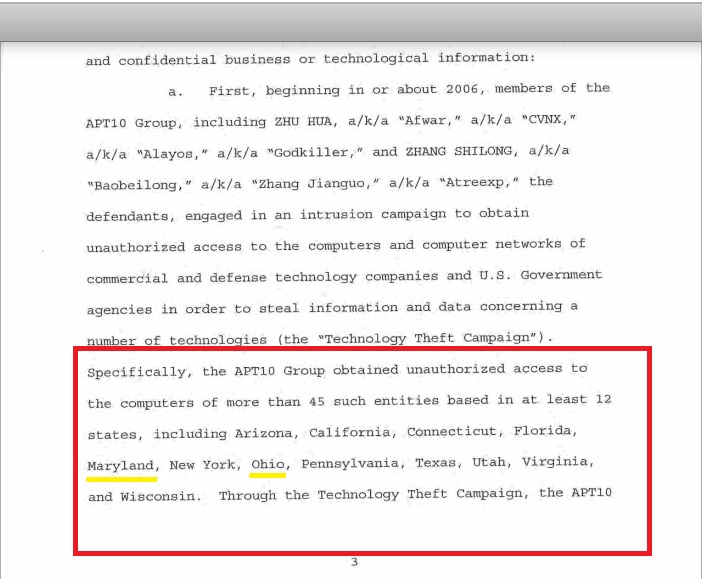
Those images are screenshots from the indictment. Taken out of context the images and the parts we’ve underlined might seem a bit strange. But, basically, we’d like to know exactly what data the hackers got from the US Navy.
Unfortunately, since the DOJ hasn’t unsealed any further details from the investigation, we’re unlikely to get that fine a view. But, here, even a coarse view would help. What states were Navy computers breached in?
Depending on which bases the computers hacked were located at and how much data was stolen, the possibility exists that such an extended espionage campaign could have given China the equivalent of a “remove fog of war, display all units” cheat-code by now.
Let me explain.
The Defense Finance and Accounting Service has an office located in Cleveland, Ohio. If you wanted to know when a sailor started and stopped receiving combat pay, this would be the place to hack.
US military doctors train at Bethesda, Maryland, where they receive their first orders upon graduating from the Uniformed Services University of Health and Sciences. If an adversary wanted to know where support units were headed (and thus the proximity of the units they support) spear-phishing a Navy Lieutenant with an MD in Maryland wouldn’t be a bad idea.
That’s the rub: we’re not sure what facilities were hit, but we know that nearly 1 in 3 sailors’ info was exposed.
Still, let’s not blow this out of proportion. You could make a scary argument for any of the states hit (Connecticut has a nuclear submarine training base, most sailors deploying for the Middle East leave out of San Diego, California). The point is, it’s downright spooky that none of the major news outlets — or the indictment itself — mentions any concern over stolen intelligence.
TNW reached out the US Navy for more information. Lt. Cmdr. Liza Dougherty, Navy spokesperson, told us:
The Navy takes any incident concerning personally identifiable information very seriously, and ensures that all affected Sailors are notified immediately when an incident occurs. Due to the ongoing investigations, we are unable to provide any additional information at this time. Until the case is adjudicated we refer you to the Department of Justice for more information.
We asked if she could confirm or deny whether Cleveland or Bethesda were hit by the attack campaign, but she wasn’t at liberty to discuss the matter further.
And, if we’re being honest, that makes sense. We’re glad she didn’t offer up information just because we asked. It’s important for the US Navy to keep its cards close to its chest: the military gets a pass when it comes to transparency. Duh.
But, if we can’t be sure that the data wasn’t just Navy softball sign up sheets and Sailor of the Month shortlists, there’s far more reason for concern than just the ongoing saga of Chinese intellectual property-theft.
Nearly 20 years ago, while I was still in the Navy, I attended a security briefing where an intelligence expert explained how the enemy could use tiny slivers of information — like whether a Chaplain had arrived on base — to determine troop locations. We were always told that “unclassified” information was as valuable to the enemy as top secret information, if that information could be used to pinpoint a specific sailor.
Imagine what Chinese machine learning specialists could do with access to the internet and the personal information of 100,000 US Navy sailors (and whatever additional context came with that data). Imagine what the Chinese government — and any entity it’s willing to share with — could glean about the location of the other (approximately) 230,000 US Navy sailors by connecting the dots between them and the 100K it has info on now.
If the worst thing that happens is 100K sailors had their identity stolen by hackers trying to make a buck, and US technology secrets leaked again, this will be a bad thing. Let’s hope it’s just a bad thing.
TNW reached out the DOJ but didn’t immediately receive a response.
Get the TNW newsletter
Get the most important tech news in your inbox each week.




